- Capabilities
-
-
- For Business
- Red Team & Penetration TestingPut the security of your systems to the test
- Digital ForensicsRetrieve evidence of malicious software, criminal activities, and misuse
- On-Demand ISSOAccess proven cyber experts on an on-demand basis
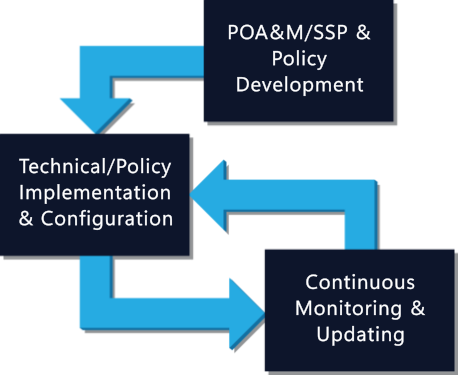
- Policy DevelopmentCraft policies for better security and regulation compliance
- CMMC/DFARS ComplianceGet tailored solutions for achieving CMMC/DFARS compliance
- For Business
-
-
- Company
-
- Resources
-
-
-
Recent Posts
- Mission Multiplier Named a Best of Huntsville Company for 2023
- Celebrating Community Support – Mission Multiplier Honored by R. Fathers M.A.D.
- Zachary Griffin of Mission Multiplier Receives Award from Athens State University
- Mission Multiplier Named Best Place for Parents to Work 2023
- Mission Multiplier Wins $43.8M Prime Contract Supporting USAF AMC to Provide Logistics Integration and Weapon System Logistics Network Support
-
-
- Employees
- Careers
Menu
Menu